Two Main Types Of Keys
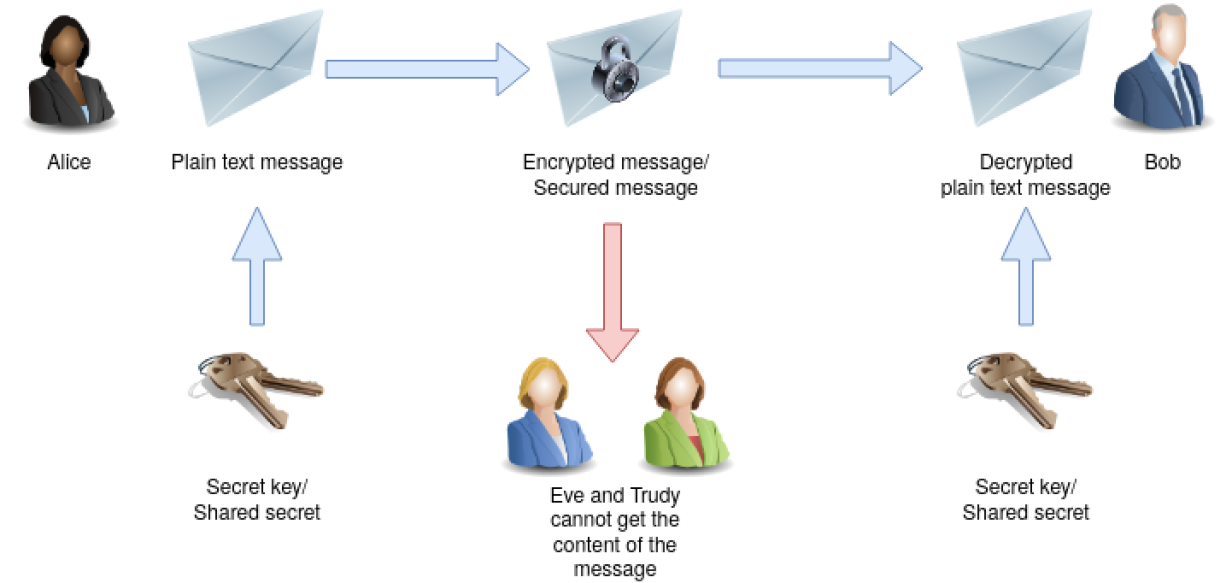
Symmetric-key
In symmetric-key schemes, the encryption and decryption keys are the same. Communicating parties must have the same key in order to achieve secure communication.
The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-key encryption, in comparison to public-key encryption.
However, symmetric-key encryption algorithms are usually better for bulk encryption. Asymmetric-key encryption is often used to exchange the secret key for symmetric-key encryption.
With exception of the one-time pad they have a smaller key size, which means less storage space and faster transmission. Symmetric key algorithms have the advantage of being pretty fast. On the downside, it’s difficult to distribute the shared secret to the communication partners.
Symmetric-key algorithms require both the sender and the recipient of a message to have the same secret key. All early cryptographic systems required either the sender or the recipient to somehow receive a copy of that secret key over a physically secure channel.
Nearly all modern cryptographic systems still use symmetric-key algorithms internally to encrypt the bulk of the messages, but they eliminate the need for a physically secure channel by using Diffie–Hellman key exchange or some other public-key protocol to securely come to agreement on a fresh new secret key for each session/conversation (forward secrecy).
Symmetric key encryption
Public-key (asymmetric-key)
In public-key encryption schemes, the encryption key is published for anyone to use and encrypt messages. However, only the receiving party has access to the decryption key that enables messages to be read.
Two of the best-known uses of public key cryptography are:
- Public key encryption
- Digital signatures
Public key encryption
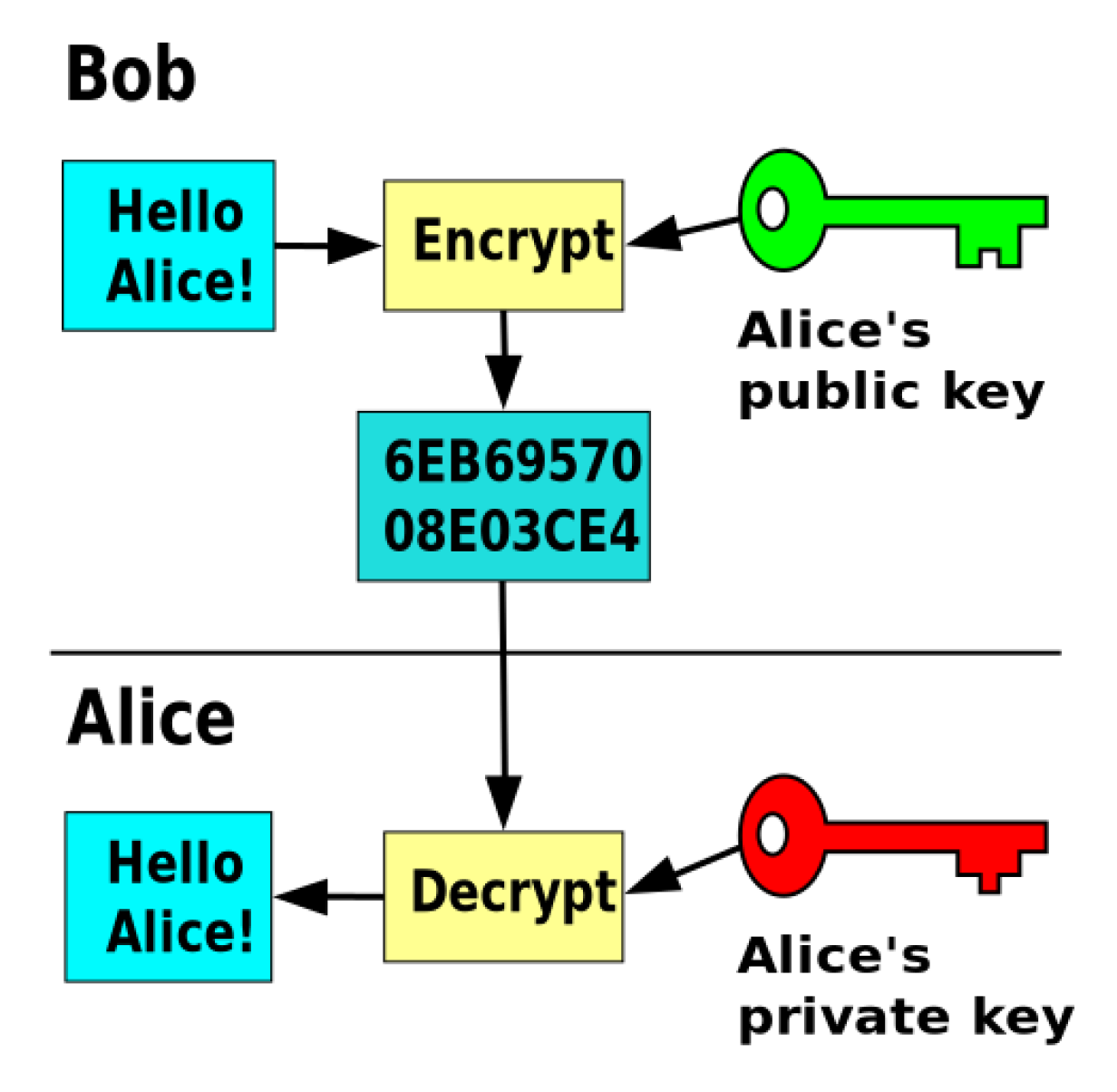
In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message. The security of the system depends on the secrecy of the private key, which must not become known to any other.
When Alice and Bob want to use public key cryptography to communicate, they have to exchange their public keys and are good to go.
Digital signatures
How could Bob check if this message really came from Alice and wasn’t changed on the way to him?
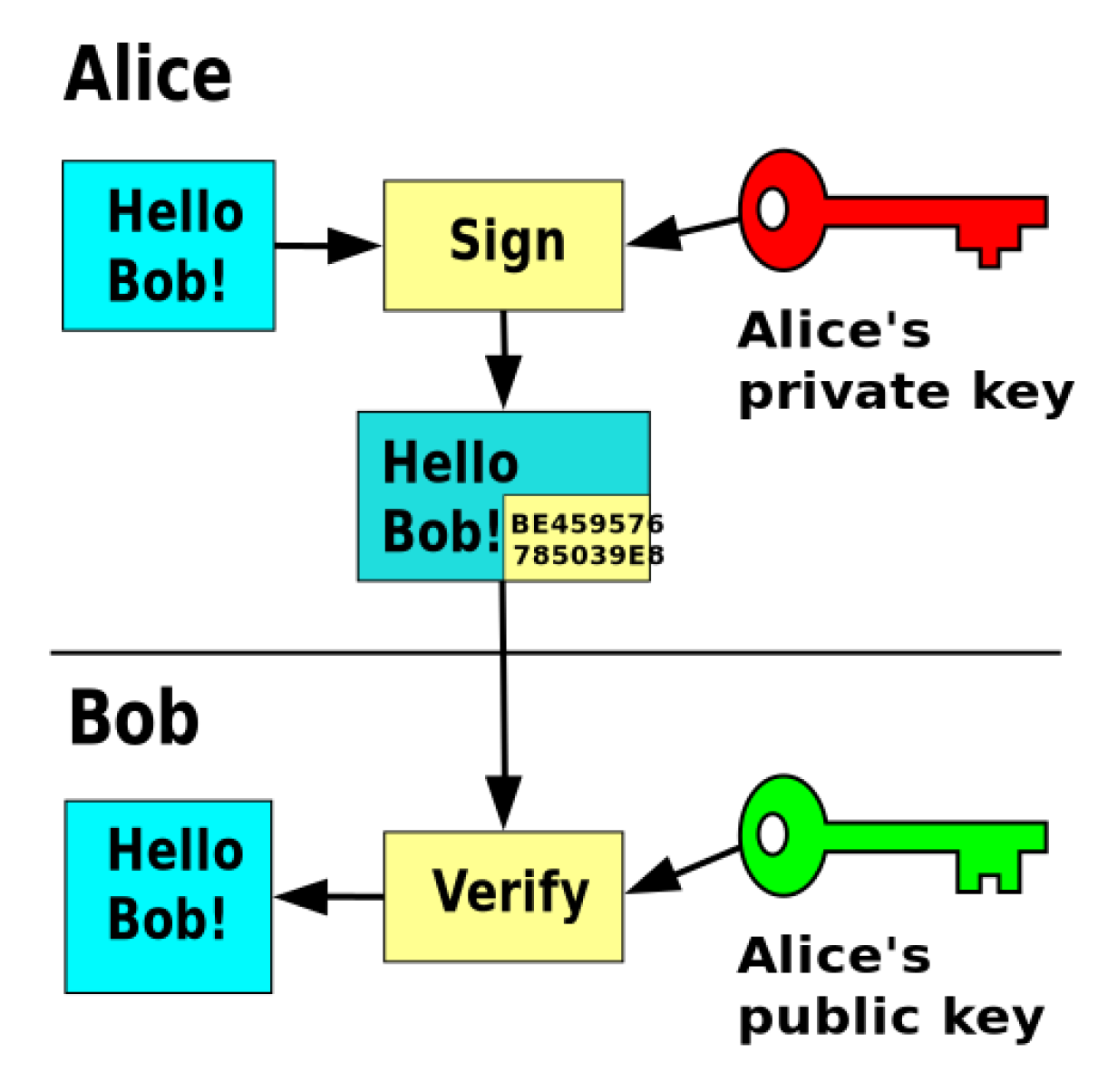
In this example the message is digitally signed with Alice’s private key, but the message itself is not encrypted. 1) Alice signs a message with her private key. 2) Using Alice’s public key, Bob can verify that Alice sent the message and that the message has not been modified.
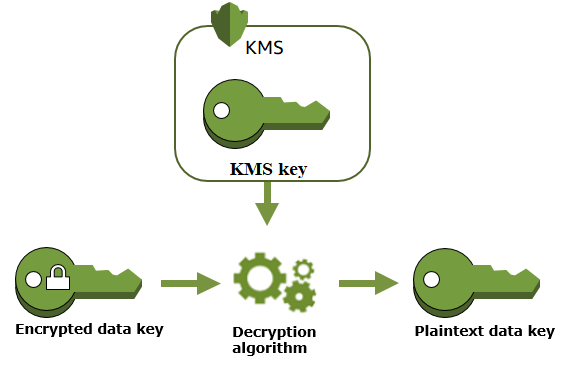
Key Management Service
Envelope encryption
When you encrypt your data, your data is protected, but you have to protect your encryption key. One strategy is to encrypt it. Envelope encryption is the practice of encrypting plaintext data with a data key, and then encrypting the data key under another key.
This top-level plaintext key encryption key is known as the root key.
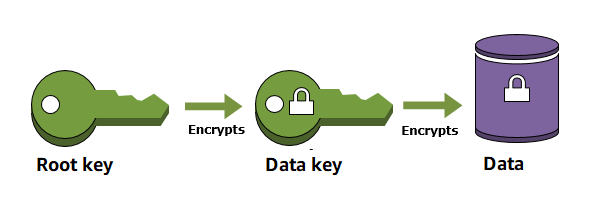
Data keys
KMS generates, encrypts, and decrypts data keys. However, KMS does not store, manage, or track your data keys, or perform cryptographic operations with data keys. You must use and manage data keys outside of KMS.
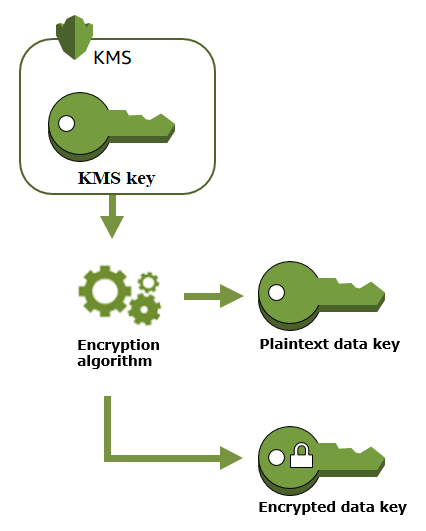
Create a data key
KMS generates the data key. Then it encrypts a copy of the data key under a symmetric encryption KMS key (root key). The operation returns a plaintext copy of the data key and the copy of the data key encrypted under the KMS key (root key).
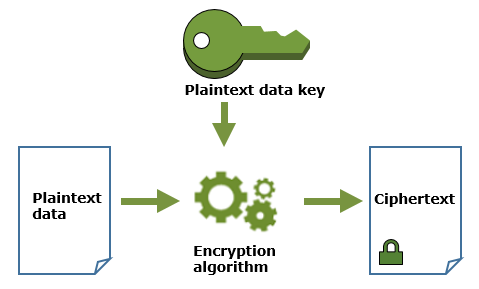
Encrypt data with a plaintext data key
After using the plaintext data key to encrypt data, remove it from memory as soon as possible. You can safely store the encrypted data key with the encrypted data so it is available to decrypt the data.
Decrypt data with a encrypted data key
To decrypt your data, pass the encrypted data key to the Decrypt operation. KMS uses KMS key (root key) to decrypt the data key and then returns the plaintext data key. Use the plaintext data key to decrypt your data and then remove the plaintext data key from memory as soon as possible.